
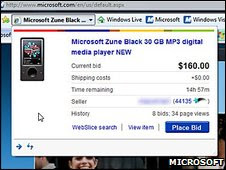
On April 1, a computer worm called Conficker, which has already infected millions of machines worldwide, is expected to do something bad, though no one knows exactly what. Some experts fear that an army of infected machines could be ordered to launch a coordinated attack or send out a barrage of spam. But a tool released today could help lessen the impact by allowing big companies and institutions to quickly weed out infected machines by scanning entire networks for signs of infection.
Analysis of the Conficker worm has previously revealed that infected computers will "phone home" on April 1 to receive a new set of instructions. It is already possible to detect the worm by scanning machines individually, but this is a relatively time-consuming process. It's also possible to detect the bug by watching for outgoing communications sent across a network, but the latest version of Conficker is designed to stay silent until April 1.
Dan Kaminsky, director of penetration testing for the Seattle-based security company IOActive, helped create the new scanning tool and says that it can identify an infected machine by recognizing the way it presents itself to the wider network. This makes it quick and easy to scan for the worm remotely and does not require any special access to machines. "It's like driving through a neighborhood looking for houses with big signs on their doors," Kaminsky says.
The tool was created after Tillmann Werner and Felix Leder, members of an independent research organization called the Honeynet Project, asked Kaminsky to review their research on Conficker. The pair had figured out that the worm changes the way a machine appears on a network. Kaminsky seized on this, suggesting that the researchers create a tool that uses this information to find infected machines. The researchers built such a tool and worked through the weekend to get it ready for broad distribution to suppliers of other security software. "Whatever vulnerability scanner a company is using, it should have support for this by the end of the day," Kaminsky says.
Bruce Schneier, chief security technology officer at BT Counterpane, says the new tool's ability to seek out the virus remotely should be useful, since it will let people scan a huge number of machines very quickly. This is important, Schneier says, because the worm is such a nasty pest. "Conficker is an extremely well-written, extremely well-designed, extremely well-executed worm," says Schneier. "It really is an impressive piece of work, and there's someone really smart behind it." But Schneier adds that it's important for computer users and administrators to protect their machines against a variety of malware, not just a single threat.
"If you've been running a good environment, you shouldn't be worried about this," says Rich Mogull, founder of the security-consulting company Securosis, who helped connect the Honeynet researchers and Kaminsky with network-security vendors over the weekend. Mogull notes that Microsoft has already released several patches that block the vulnerability that Conficker uses to infect a machine. However, he says that companies worried about Conficker should start scanning for it right away, after checking to see if their network-security tools have been updated.
Kurt Rohloff, a scientist who studies Internet worms at the research and development company BBN Technologies, says that the tool could prove useful, though he doubts that there's time to find and neutralize every computer infected with the worm. Rohloff says that the new scanner could be used to take preventive action by identifying infected hosts and removing them from the network, though he admits that this approach is "drastic, because you're removing connectivity."
Kaminsky notes that the tool is intended for organizations with large networks. For individuals, he says, the best approach is to make sure that the latest security updates are installed and up-to-date antivirus software is running. Since Conficker blocks a computer from accessing certain security websites, users could test for the worm by trying to visit those sites, Kaminsky says. Werner and Leder plan to release a paper within the next day, describing the technical details of their discovery.






























 La Vecchia explained at this year’s Geneva Motor Show that the so-called Flow Accumulator Energy Storage (FAES) invented by NLV is a combination of an electro-chemical battery and a redox cell. Each 15-20 minute charge will last you well over 300 miles, that’s ridiculous… yes I know. Remember, its fully electric, not hybrid.The price of this green monster? Nothing has been said just yet, but considering the technology put into this, you will need to be pretty darn rich to be this ‘green’. Here are a few mouth watering pictures below…!
La Vecchia explained at this year’s Geneva Motor Show that the so-called Flow Accumulator Energy Storage (FAES) invented by NLV is a combination of an electro-chemical battery and a redox cell. Each 15-20 minute charge will last you well over 300 miles, that’s ridiculous… yes I know. Remember, its fully electric, not hybrid.The price of this green monster? Nothing has been said just yet, but considering the technology put into this, you will need to be pretty darn rich to be this ‘green’. Here are a few mouth watering pictures below…!














